How Can Phishing Attacks Hurt Your Business?

Based on the 2016 edition of Ponemon’s annual Cost of Cyber Crime report, phishing is now one of the most prevalent cyber-attacks today. Should you be worried about it? It depends. If you think any of the consequences of phishing attacks outlined below can impact your business, then maybe you should be.
Tarnish your company’s image
Most phishing attacks are designed to steal personal information. The way cyber criminals do this is by crafting legitimate-looking emails that compel recipients into disclosing their personal details.
So, for example, you might receive an email from your bank informing you of a security upgrade that requires you to update certain personal information, like:
- your full name,
- bank account number,
- address,
- phone number
- your online username and password
To update your personal details, you typically need to click a link on the email body and enter the required information on a form on a website that looks just like your bank’s site.
Of course, although both appear to be genuine, the email is really fake and the website is really just a spoofed version of your bank’s website. When you enter your personal details on the form, they’ll just end up in the hands of cyber criminals.
So how can a phishing attack like this damage a company’s reputation?
If it’s your website that’s spoofed in a phishing campaign, your company’s reputation can take a hit. It won’t be easy for identity theft victims to dissociate your organisation from the attack if, later on, it’s discovered their personal information was actually stolen at a site closely resembling your own.
Immediately after the attack is somehow exposed, some customers (or potential customers) might become too spooked to continue transacting with your site.
Disrupt operations

Instead of hyperlinks that redirect victims to a malicious site, phishing emails can also be accompanied by malicious attachments. These payloads are usually harmful malware such as trojans, keyloggers, botnet clients, and (the most common phishing payload these days) ransomware. Once these malware are able to enter your network, they could potentially cripple business operations.
Ransomware, for instance, can encrypt files, hard disks, or even entire networks and hold your business captive until you pay the ransom. Botnet clients, on the other hand, can stay hidden for a long time, consuming precious network bandwidth and computer resources until they’re discovered.
Steal your business’ identity
Phishing attacks are usually associated with identity theft. But while most of the attention is focused on stolen ‘personal’ identities, business identities are also at risk. In the realm of small and medium-sized businesses, where various personal assets (including funds, credit, and certain personal information) are often interlinked with the business, ‘personal’ identity theft can easily escalate into business identity theft.
Once fraudsters are able to hijack your business’ identity, they can obtain credit cards, purchase goods and services, divert funds, or even ruin business relationships - all while making it appear these were your organisation’s own doing.
Leave you vulnerable to more sophisticated attacks
Some spear phishing attacks are targeted at individuals with administrative privileges in the corporate network. If these attacks succeed, attackers can gain the ability to bring down defences and/or establish persistence, which will allow them to come and go as they wish or remain undetected in your network for a longer period of time.
While inside, the infiltrators can conduct other privilege escalation activities, carry out a massive data breach attack, uncover trade secrets, or do other things that can cause irreparable damage to your business.
Siphon resources from business operations
The moment you discover your company has become an unwitting accomplice to a phishing attack (like if your website is spoofed or if your machines are ensnared in a spam botnet that sends out phishing emails), you might be left with no choice but to redirect a substantial amount of financial and human resources to:
- Notify customers who might have been or likely will be victims of identity theft;
- Comb your network for botnet malware infections and perform malware removal;
- Acquire more advanced cybersecurity solutions; and
- Conduct training and workshops to educate users of malware prevention best practices.
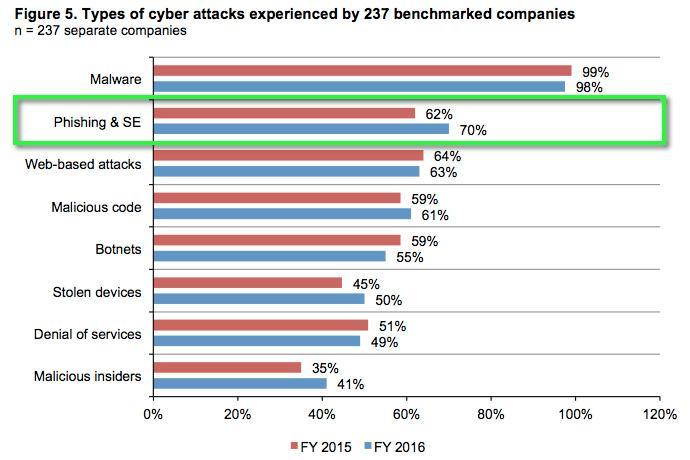
Phishing attacks are on the rise
With incidents of phishing and social engineering (SE) attacks on the rise (as per Ponemon’s 2016 Cost of Cyber Crime Study), it’s imperative for businesses to address the threat before it hits them.
Phishing and social engineering attacks rose from 62% in 2015 to 70% in 2016 - Ponemon 2016 Cost of Cyber Crime Study
The best way to thwart phishing and social engineering attacks is through a combination of end-user education and the application of anti-phishing solutions. If businesses have in-house security experts, then these people should be charged with the task of incorporating phishing and SE countermeasures into the corporate security program. If the organisation doesn’t have the needed expertise, then cybersecurity consultants should be contacted for professional assistance.
Related Posts
By accepting you will be accessing a service provided by a third-party external to https://www.htl.london/