This Is How A Drive By Download Sneaks Malware Into Your System

There used to be a time when it was relatively easier to prevent malware from infecting our systems. We’d install an antivirus, keep its database updated, and equip end users with a laundry list of things to avoid - like suspicious email attachments and unfamiliar websites. Today, drive by downloads are making malware avoidance a more challenging task.
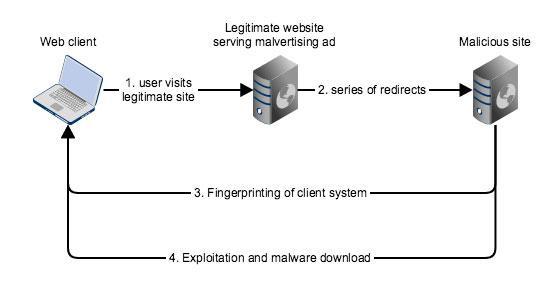
A drive-by download is a malware infection procedure that doesn’t require the user to download anything or even click a link. For his/her system to get infected, the user only has to visit a site that’s been compromised. The infection process then takes place behind the scenes, without the user ever noticing anything unusual.
To make matters worse, the sites that are being compromised now include popular, reputable domains. Last year, one of the attacks involving drive-by downloads included high traffic websites like AOL, BBC, NFL, and the New York Times. The aggregate visitor traffic from all these sites amounts to billions. Even popular e-commerce sites like Amazon haven't been spared.
Malvertising and redirections
But how do these reputable sites become sources of malware in the first place? Technically, they’re not the “source”. Rather, they’re more like unwitting accomplices. Although popular sites are certainly not immune from hacking and can be forced to serve malware directly after getting hacked, this isn’t what usually happens.
What mostly happens is that attackers contaminate these sites by tampering the ads being served on their pages. This cyber-attack technique is known as malvertising. Although there are other ways of compromising legitimate sites, such as cross-site scripting (XSS) or SQL injection, malvertising is the most common. In a malvertising campaign, attackers hack into an advertising network’s servers and then inject surreptitious code into the network’s ads.
As soon as these malicious ads are served (some of which, to reputable sites), whoever views them is subjected to a series of redirections that eventually lead to a site owned by the attackers. It’s here where the download process takes place. The unauthorised downloads are able to commence after the attackers manage to exploit vulnerabilities in the user’s web client application (in most cases, a web browser like Chrome, Internet Explorer, Firefox, or Safari).
Exploiting browser and plugin vulnerabilities
Before any vulnerability exploit or malware download ever takes place, the attacker carries out a technique known as fingerprinting. Fingerprinting enables the attackers to obtain information that will help them determine how (or if ever) to proceed with the attack.
This information, which is typically about the user’s browser, OS, plugins (e.g. Flash, Silverlight, Java, ActiveX, etc), and their respective versions, among others, will help identify vulnerabilities existing in the user’s system. Once the vulnerabilities have been identified and exploited, the download commences.
Some of these vulnerabilities are zero-days. That is, vulnerabilities that have not yet been discovered by the software developers and, hence, have not yet been patched. Attackers take advantage of zero-days to evade traditional virus protection solutions, making zero-days serious vulnerabilities.
However, there are also vulnerabilities that, even long after having been identified and a patch released, still exist in the software for the simple reason that the user or whoever is tasked to do it has not yet updated the software and (subsequently) applied the patch.
That’s correct. The seemingly mundane task of updating your OS, browser, and browser plugins, which may include security updates, could actually save you from drive-by downloads.
Commodifying drive-by download attacks through exploit kits
All these techniques, i.e. malvertising, fingerprinting, vulnerability exploitation, and malware download, used in drive-by downloads are now packaged into a single toolkit known as an exploit kit (EK), a cyber-attack product sold in hacking forums and other dark corners of the Web. Some of the most notorious exploit kits that have affected millions of victims include Angler, Rig, Neutrino, and Blackhole EK.
Most of these exploit kits are delivered as-a-service, just like many cloud-based services. That means non-technical cybercriminal organisations can simply pay a monthly subscription and be able to launch drive-by download attacks.
A typical EK service usually includes:
- a user-friendly graphical UI,
- a collection of exploits (an ‘exploit’ is usually JavaScript code that exploits a specific vulnerability),
- a selection of payloads (the malware to be downloaded, e.g. trojans, keyloggers, ransomware, worms, etc.),
- EK software updates,
- And even technical support
Some highly advanced exploit kits are even equipped features that allow them to detect virus protection solutions and abort the attack if any is found.
Conclusion
Because of their ability to ensnare a large number of victims while evading detection, drive-by downloads have become the favorite method of cybercriminals for infecting systems with malware. In order to counter such highly sophisticated attacks, you need to ensure your systems are constantly updated, arm your network with solutions that work against zero-days, or contact a reputable internet security services provider who can put together a cost-effective strategy.
Related Posts
By accepting you will be accessing a service provided by a third-party external to https://www.htl.london/