This Is What Happens When You Don’t Take DNS Security Seriously

When businesses embark on cyber security initiatives, one of the things that’s often overlooked is DNS security. Many people forget or simply aren’t aware that a compromised DNS infrastructure (or any critical component of that infrastructure) could potentially lead to considerable downtimes, malware outbreaks, data breaches, and several other forms of cyber incidents.
These things can happen because DNS or the Domain Name System plays a crucial role in almost any user-initiated activity that takes place on the Internet. DNS is in charge of resolving the easily-recognisable names like www.somesite.com or ftp.companyx.com that users enter into their web browsers, email clients, or file transfer clients into the IP addresses (e.g. 200.100.10.10) that computers use to communicate with one another.
It seems like a simple task. But if that translation process is broken, client applications can’t reach the services they’re meant to connect to. As a result, customers can’t view your website, employees can’t send out emails, business partners can’t download files from your file transfer server, and so on.
Denial of Service attacks on DNS services
This is basically the intention when shady characters launch Denial of Service (DoS) attacks on DNS services. The attacker’s goal is to prevent users from accessing an organisation’s online services.
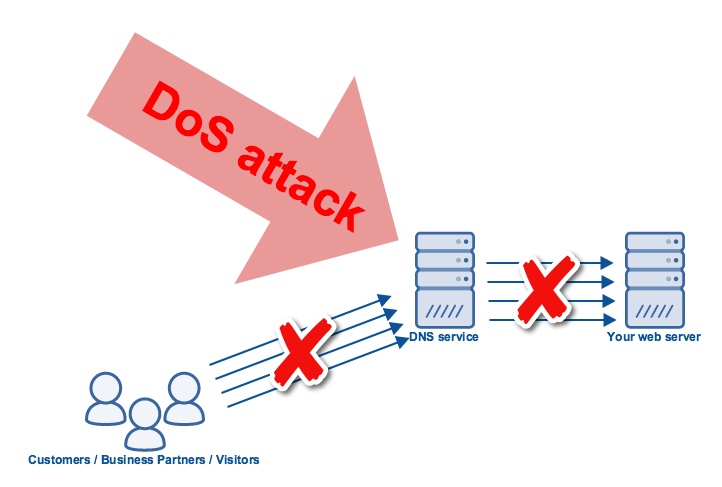
DoS attacks on DNS infrastructures have become even more disruptive lately. One reason is that most companies now delegate their DNS operations to a service provider. If that provider is subjected to a massive DoS attack, the majority if not all of its customers could be affected by the attack.
Another reason is that DoS attacks themselves have grown so large, some of them could overwhelm even the biggest DNS providers. The massive Distributed Denial of Service (DDoS) attack on Dyn, one of the largest DNS service providers in the world, crippled numerous online sites because all those sites’ DNS operations were hosted on that particular provider.
Theoretically, companies can mitigate this particular threat by subscribing to multiple DNS providers. Of course, economics will have to be taken into consideration, as doing so would certainly entail a larger expense. Businesses will need to determine whether the ability to avoid possible loss of opportunity and revenue in the event of a DDoS attack is truly worth the cost of buying multiple DNS services.
DNS hijacking
Denial of Service attacks, which threaten DNS availability, aren’t the only threats against the Domain Name System. There are other threats as well, like threats to DNS record integrity. For example, hijackers can tamper DNS records so that they map names to IP addresses of malicious servers.
Once victims are redirected to those servers, they could be subjected to a variety of attacks. The type of attack will largely depend on the type of site whose domain name was hijacked. For instance,
- If it were an online banking site, victims could be defrauded;
- If it were an e-commerce site, the victims’ personal information or credit card data could be stolen;
- If it were a popular news site, victims could be redirected to exploit kits, which in turn drop different kinds of malware.
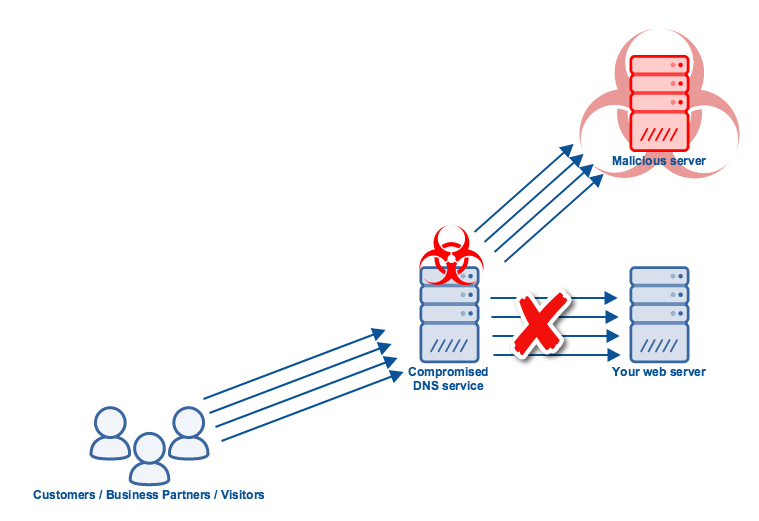
End users aren’t the only victims in a DNS hijacking attack. The businesses who own the hijacked domain names are victims here as well. As soon as word spreads of people getting victimised when they connect to certain sites, the reputation of those legitimate sites can be damaged.
People might refrain from visiting those sites for some time. This can lead to fewer transactions or, in the case of news sites, a drop in readership. In any case, the business will suffer.
Internal threats to DNS
The threats we’ve mentioned so far refer to external threats aimed at external DNS servers. But DNS threats can also originate internally and can be aimed at internal DNS servers. Certain types of malware that connect with remote command-and-control (C&C) servers, for instance, use DNS as their means of communication.
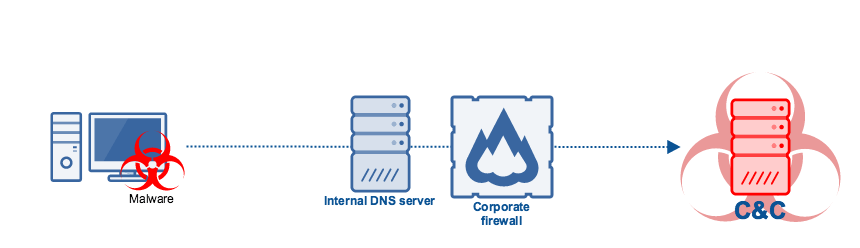
Botnets, banking trojans, and ransomware are just some of the malware types that connect to C&C servers to receive commands or upload stolen data. These threats can bring down the performance of your internal network, steal data (e.g. personal information, trade secrets, credit card data, financial data, etc.), or cripple your systems.
Internal threats are hard to detect using traditional network security solutions. You’ll need to employ a DNS firewall or any similar solution specifically designed for DNS traffic in order to counter them.
Many organisations take DNS security for granted. But considering how important DNS is to a lot of business processes and how much damage can be made if DNS infrastructure is exploited, that outlook towards DNS should really change.
Related Posts
By accepting you will be accessing a service provided by a third-party external to https://www.htl.london/